
Pylar
Securely connect your entire data stack to any agent
681 followers
Securely connect your entire data stack to any agent
681 followers
Pylar connects agents to your data stack, safely. Connect to any datasource, define exactly what an agent can see, turn those views into custom MCP tools, and publish them to any agent builder - with full observability across every AI deployment.






Pylar
👋 Hey everyone, I'm Hoshang, Co-founder of Pylar.
Super excited to finally share what we’ve been building.
Agents today are great at reading docs, invoices, websites, transcripts -
but the moment you want them touching structured systems where sensitive customer data is stored e.g Snowflake, Postgres, CRMs… things get tricky.
We kept hearing the same two blockers over and over:
Agents may over-query and silently spike warehouse bills
Agents are at a risk of leaking sensitive data (PII, financials, customer history) because access isn’t properly scoped
And right now, teams have two options:
- Off-the-shelf MCP servers : 18,000 exist, ~10% are malicious, and most are exploitable or too generic for production.
- Custom API wrappers : months of engineering bandwidth used up in building endpoints, policies, and governance… all brittle, fragmented, and hard to audit.
This forces companies into a painful choice: lock agents down so much they become useless, or open things up and risk a security incident.
Traditional database ACLs weren’t designed for autonomous systems. Custom APIs are hard to build, govern and control for agent level interactions.
Pylar exists to fix this. It’s a governed access layer between your agents and your entire data stack.
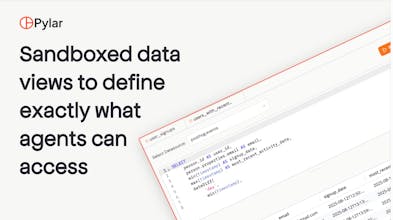
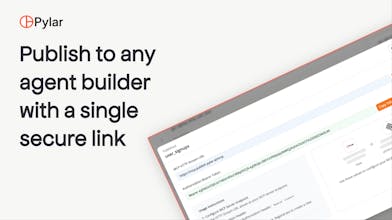
You connect your datasources → define sandboxed SQL views → turn them into MCP tools → ship them to any agent builder… all from one control plane, with full observability.
What you get out of the box:
Agent-specific sandboxed views (never raw DB access)
Enforced permissions & guardrails
Automatic breach containment + audit logs
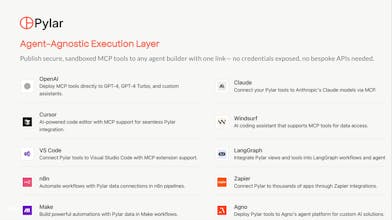
Publish to any agent builder (n8n, Cursor, Claude, LangGraph, etc.) via a single secure link
We’re already working with some fantastic data, platform, and security teams - everything from internal analytics copilots to customer-facing AI features wired directly into production data.
If you’re exploring structured-data access for agents, I’d love to hear your thoughts, help you build your use case or just share best practices on what we've been seeing with our customers. You can book a call with me here if you'd like.
Thanks for checking us out — means a lot. 🚀
- Hoshang
Co-founder, Pylar
@hoshang_m Love that you’re tackling agent over‑querying, feels like a pain everyone’s quietly dealing with right now.
Pylar
@masump Thanks for the support! And yes, as companies go deeper into agent use-cases, this is where most projects get stuck. Agents operate at machine scale, so one bad query can have a much bigger impact than a human ever would.
Claude-Mem
@masump @hoshang_m my solution for over querying is strict progressive disclosure rules in my search skill (for Claude-Mem)
Search and get indexed list, select data to read, contextualize data by getting a timeline of activity at those observation points, then read summary level information.
But that’s structured and requires thought in the way the data is created and stored vs. this tool which lets you access anything from any source! Which is really really cool that it does that :)
How does it handle over querying and context window limits?
Visla
@hoshang_m Congrats! Great launch!
Pylar
@hoshang_mReally interesting problem space — and honestly, one that’s becoming more pressing as teams try to push agents beyond simple document Q&A.
You nailed the two blockers perfectly: cost explosions from uncontrolled queries and the real security risk of giving agents broad access to sensitive systems. Both are major reasons adoption stalls in enterprise environments.
I like that Pylar sits between “generic MCP servers that aren’t production-ready” and “months of building brittle custom wrappers.” That gap is very real.
Excited to see how you handle policy enforcement and auditability as things evolve. Congrats on the launch — feels like the right product at the right time.
Product Hunt Wrapped 2025
Finally, someone tackling the agent-to-DB mess. I’ve nursed a painful Snowflake bill from a runaway agent. Sandboxed views + audit logs feels sane. How do you cap query spend per agent? Might wire this into Cursor first, then LangGraph if it holds up.
Pylar
@alexcloudstar Thanks Alex! Right now, we cap spend in two ways:
1. Every agent only sees a sandboxed view, never your raw warehouse.
So even if it tries something wild, it can’t fan out into expensive tables or join half your schema.
2. Query-level guardrails on the tool itself.
We let you set limits on row counts, frequency, and even block certain patterns (e.g. unscoped scans) via policies. If an agent tries to exceed it, Pylar shuts it down and logs the attempt.
On top of that, you get full audit logs + costs per tool call so you can see exactly which agent is expensive before the bill shows up.
Looking forward to having you try us out!
Pylar
@vouchy Thanks for the question, Van! Instances of agents leaking sensitive data is on the rise, recently Salesforce had a security incident where their ai agents accidentally leaked sensitive crm data through through their agentforce powered web-to-lead form. attackers injected a malicious prompt on website forms to make the AI share internal data with outside domains.
basically, hiding malicious instructions inside normal text. the ai read it… and pulled private data it had permission to see. I did a deep dive here, you might find this interesting - https://www.pylar.ai/blog/forcedleak-salesforce-agentforce-vulnerability-deep-dive
Custom APIs are a nightmare and MCP servers are a minefield. This feels like the first real governed layer built for agents. Good work!
Pylar
@zerotox Thanks for your support!
Nas.io
How do you monitor agent behavior across different builders (Cursor, LangGraph, n8n, etc.) from one place?
Pylar
@nuseir_yassin1 Our evals layer helps you measure how different agents across platforms like Cursor, LangGraph etc are interacting with your internal data.
Because of that, you get a single place where you can see:
what each agent is querying
how often it’s hitting your data
what was allowed vs blocked
and any odd behavior you should know about
So even if one agent is in Cursor and another is in LangGraph or n8n, all their activity shows up in one dashboard.
Also, if you update a data view, a rule or add more mcp tools in Pylar - every agent using it automatically follows the new version.
More on this here - https://docs.pylar.ai/learn/evals/evals-dashboard
Does this help?
Does Pylar throttle or rate-limit agent queries in any way? Congrats on the launch.
Pylar
@himani_sah1 Great question and thanks for the support. Rate limiting queries is going to be live on the product next week, but for now you can set additional guardrails like row limits and scoped filters with policies between your data and the mcp tools so an agent can’t over-query or wander outside the slice of data you’ve exposed. And every attempt gets logged so you can see if an agent is starting to push its boundaries.
CodeBanana
@vishalbajaj Great product! All the best for your launch 🎉
Pylar
Airbook AI
@zethleezd appreciate your support Zeth