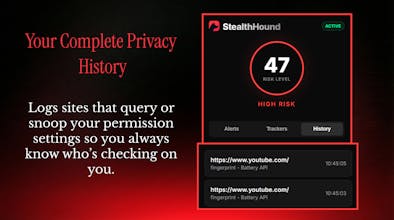
StealthHound exposes and blocks hidden browser fingerprinting and silent tracking in real time, even without cookies or logins. Get instant risk signals (Low/Medium/High), live alerts, and automatic blocking of invasive techniques like canvas fingerprinting, API abuse, and hardware probing. Runs fully locally with zero data collection and no browser slowdown. See who’s tracking you, how they do it, and shut it down before profiling starts







Proximity Lock System
We are finally getting out of beta after working on StealthHound for more than 3 months.
The main idea came from a simple gap we noticed: on our phones, we can clearly see which apps use which permissions but on the web, we have almost no visibility into what websites access or track in the background.
Websites silently use fingerprinting and browser APIs to identify devices without consent. StealthHound brings app-like permission visibility to the browser with real-time risk signals, live alerts, and automatic blocking of invasive tracking, running fully locally with zero data collection.
Website: https://stealthhound.netlify.app/
We’d love your feedback and thoughts. Thanks for supporting an indie launch 🙌
@akarshjha03 Hi Akarsh, love this idea and congrats on the launch. How does this impact memory? I already have +fan_noise as a constant soundtrack from multiple sub processes.
Proximity Lock System
@zolani_matebese Great question, and thank you!
StealthHound doesn’t run continuous background analysis, it operates on on-demand instrumentation triggered by specific APIs commonly used in fingerprinting. This keeps memory stable and avoids persistent CPU usage, so it won’t contribute to constant fan activity.
we’re actively profiling to keep fan noise and background load as close to zero as possible. Performance-first was a non-negotiable for us.
@akarshjha03 That's a nice solution. Congrats on placing in top5!
PicWish
@akarshjha03 interesting tool. how does this compare to brave's shields regarding audio context fingerprinting?
Proximity Lock System
@mohsinproduct Good question. Brave Shields mitigates audio fingerprinting at the browser level via randomization, so fingerprints become unreliable. StealthHound instead detects and surfaces audio fingerprinting behavior per site, giving visibility and control without global API modification.
Proximity Lock System
@revenue_ops Thanks! 🙌
The first “aha” is seeing live fingerprinting signals light up on sites people already trust canvas, audio, or WebGL activity happening quietly in the background. That moment makes it clear how much tracking is invisible by default, and why local, real-time visibility matters.
@akarshjha03 Visibility is powerful, but people tune out warnings quickly. What’s the one signal StealthHound shows that consistently makes users change behavior, something that actually gets them to block, not just notice?
Proximity Lock System
@malekmoumtaz It’s seeing high-entropy fingerprinting on sites that don’t need it. That expectation gap is what consistently turns awareness into action.
Proximity Lock System
@revenue_ops It varies. Users who land on ad-heavy or analytics-rich sites usually hit the “aha” almost immediately. Others might miss it at first if they start on quieter sites, which is why we’re actively improving onboarding to surface a clear, representative signal early without forcing noise.
Congrats on the launch! StealthHound’s real‑time fingerprinting detection and fully local, zero‑data design feel like a must‑have privacy layer for modern browsing.
Proximity Lock System
@zeiki_yu Appreciate it! 💙
Real-time fingerprinting detection running fully on-device was a core design decision no servers, no tracking, no compromises. Glad that philosophy resonated with you.
DiffSense
Hey, Love the idea! Kind of like "little snitch" but for chrome! Canvas tracking. Whats that? I never heard of it. Are many websites tracking with canvas these days?
Proximity Lock System
@conduit_design Hey, thanks that’s a great comparison!
Canvas tracking is a lesser-known fingerprinting method where sites render invisible graphics via the HTML5 canvas and extract subtle device-specific signals from it. It’s not universal, but it’s definitely used by analytics and anti-fraud tooling on many popular sites today, often without users realizing it.
Hi, does it monitor continuously, or is there any kind of scheduling?
Proximity Lock System
@jeetendra_kumar2 It’s event-driven, not continuous.
StealthHound activates only when relevant browser APIs are accessed (canvas, WebGL, audio, etc.), so there’s no background polling or scheduled scanning when nothing is happening.
@akarshjha03 Thanks for sharing.Will it be only extension or any other plateform are you going to launch
Proximity Lock System
@jeetendra_kumar2 For now, it’s a browser extension, since that’s where we can observe these signals most effectively. We’re exploring other platforms, but the extension is the focus today.
Interesting tool but I'm curious about the ethics here. LinkedIn specifically shows who viewed your profile as a feature to encourage networking - circumventing that feels a bit sketchy.
I get the use case for recruiters who don't want to tip off candidates, but doesn't this basically defeat the mutual transparency that makes LinkedIn valuable?
Also wondering about the technical side - how does this work without triggering LinkedIn's bot detection? They're pretty aggressive about third-party tools accessing their platform.
Proximity Lock System
@ahkeminozen That’s a fair question, and we’ve thought about it a lot.
On the ethics side: StealthHound doesn’t automate actions, scrape data, or impersonate users. It focuses on client-side privacy controls limiting passive signals and tracking surfaces exposed by the browser. The goal isn’t to undermine networking, but to give users agency over how much passive visibility they expose, especially when just browsing.
Technically, there’s no bot behavior involved. StealthHound runs entirely in the browser, doesn’t inject automation, doesn’t hit LinkedIn endpoints, and doesn’t bypass auth or rate limits. From LinkedIn’s perspective, it’s still a normal human session, just with fewer fingerprinting signals leaking by default.
We’re very deliberate about staying on the right side of both user intent and platform boundaries.
Really like the idea of turning something invisible into something legible.
Curious how you think about the UX tradeoff here:
once users start seeing concrete "risk signals", does it change behavior over time – or does it mostly serve as an inspection / debugging tool?
In other words, do you see StealthHound as something people keep running passively, or something they dip into when they feel "something’s off"?
Congrats on the launch – performance-first + local-only is a strong stance 👏
Proximity Lock System
@dmitry_petrakov Appreciate that “making the invisible legible” is exactly the intent.
In practice, we expect both behaviors. Early on, it acts like an inspection layer: users build intuition by seeing real signals on familiar sites. Over time, that awareness stabilizes into passive trust, where StealthHound runs quietly and only surfaces when something meaningfully deviates from a user’s baseline.
The UX goal is to avoid alert fatigue, it should fade into the background once it’s taught you how to see again.
@akarshjha03 That framing really resonates – “teach you how to see again, then fade away” is a great north star.
The idea of moving from an inspection layer to passive trust feels especially right for privacy tooling. Once awareness is internalized, constant signaling stops being useful.
Curious whether you’ve thought about making that transition explicit in the product at some point – or if you intentionally want it to remain implicit, so the tool disappears as soon as it’s done its job.
Really thoughtful approach. Appreciate you sharing the reasoning behind it.
Proximity Lock System
@dmitry_petrakov Thanks, that means a lot.
We think of StealthHound as a temporary lens, not a permanent dashboard. Early on, it’s intentionally more expressive so users can build a mental model of what “normal” vs “suspicious” looks like. Over time, as that model internalizes, the product should recede into the background and only surface when something meaningfully violates that baseline.
But now almost every website tracks users. At the very least, Google Analytics does. Are harmless tracking methods taken into account?
Proximity Lock System
@mykyta_semenov_ Yes, that’s an important distinction. Not all tracking is equal.
StealthHound isn’t reacting to basic analytics presence. We focus on high-entropy, cross-site fingerprinting behaviors that are hard to justify for functionality, not low-risk signals like standard page-view analytics.
The goal is to separate measurement from identity. Harmless or expected tracking fades into the background.