
HEXTAGON
Expending perimeter. Centralized control. Hextagon.
12 followers
Expending perimeter. Centralized control. Hextagon.
12 followers
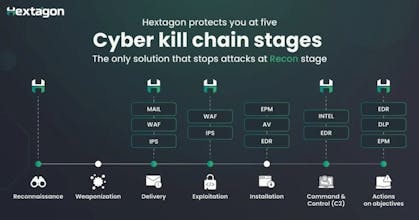
HEXTAGON detects adversary behavior in real time, disrupts threats at the earliest stages of the Attack-Chain, instantly unifies threat propagation across your entire security stack (On-Prem, Cloud, OT, and IoT), stopping breaches before they start.
Payment Required
Launch Team / Built With




A CISO perspective
We deployed Hextagon alongside our existing stack and it immediately changed how we see the perimeter. It surfaces real attacker reconnaissance and blocks it at the first move, which dramatically reduced noise and gave our SOC clear, actionable context. It feels like a security layer that finally thinks from the attacker’s side, not just another alert generator.