
Trace-AI
Know What You Ship. Secure What You Depend On.
270 followers
Know What You Ship. Secure What You Depend On.
270 followers
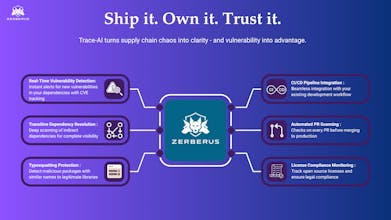
Trace-AI predicts and prevents supply-chain attacks via metadata-driven analysis of open-source dependencies, registries, and maintainer activity, no source code needed. Built by engineers who scaled to millions, it helps teams ship fast and secure.






Trace-AI
Trace-AI
A while back, when I was leading engineering teams, one of the most frustrating challenges we faced wasn’t building features; it was dealing with vulnerabilities. Every time a security report came in, it completely threw off our plans and slowed everything down.
Worse, sometimes we had to live with those vulnerabilities not because we wanted to, but because fixing them would break something else or delay critical releases. It always felt like playing catch-up with risk.
That’s really where the idea for Trace AI came from. After living through those moments too many times, we wanted to build something that helps developers and security teams get ahead of vulnerabilities, not just react to them.
Trace AI predicts exploitability - so instead of adding another alert to your inbox, it tells you which vulnerabilities actually matter before they become a problem. That shift from reactive to predictive is what we’re most excited about.
To know more https://www.trace-ai.dev/
Trace-AI
Hey Product Hunt! 👋
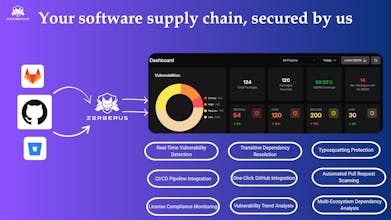
You know that moment when a critical CVE drops and you're frantically checking if you're affected? Or when you discover during a security audit that you have dozens of vulnerabilities in packages you didn't even know you were using?
That's why we built Trace-AI.
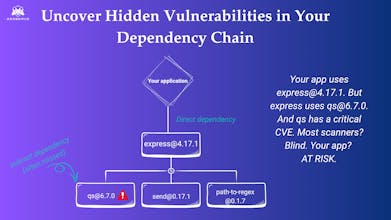
Here's the reality: Most security tools tell you WHAT is vulnerable, but not WHERE it's coming from or WHY it's in your project. You see "requests 2.25.0 has CVE-XXXX" but then spend an hour digging through dependency trees trying to figure out which of your 15 services actually uses it and whether you installed it directly or if something else pulled it in.
What actually frustrated me as a developer:
Spending more time investigating dependencies than fixing them
Getting security alerts for packages I've never heard of (transitive dependency problems)
Not knowing if I can safely upgrade without breaking something
That panicked feeling when Log4Shell happened and we had to audit everything
If you've ever looked at your node_modules or site-packages folder and thought "I have no idea what half of this is," this is for you.
Currently supported:
Languages: Python, JavaScript (Java launching next week | Go, Rust, Ruby coming soon)
Platforms: GitHub (GitLab and Bitbucket in the works)
Looking for your feedback:
Try it with 5 repos free (no card needed) plus, Product Hunt community gets 2 additional repos! Use the promo code in this launch. Let me know what breaks, what works, or what you'd want to see next.
Don't see your language or platform? Reach out directly, we actively reprioritize our roadmap based on what teams actually need. If there's demand, we'll move it up the queue.
Follow along for updates, or drop your toughest questions. Real feedback from this community is what makes products better. 🙏
Gridapps Testimonials
Congrats on the Launch Ram and Tem
Trace-AI
Thanks so much, @iamsaravanaa We're really excited about this launch would love to hear your thoughts if you get a chance to try it out!
Product Hunt Wrapped 2025
Love the metadata-first approach. Predicting risk before CVEs and no source access required fits real-world SOC workflows. The CRA alignment is a nice touch. Curious how you score maintainer behavior over time, and how noisy alerts are. Congrats on the launch!
Trace-AI
Thanks @alexcloudstar Really glad the metadata-first approach resonates it's exactly what we built for. Great questions on maintainer scoring and alert noise, let me break those down
We track maintainer health by analyzing three key signals over time:
Time since last commit
Commit frequency
Release cadence
This data is pulled from live sources like GitHub repositories. The scoring adapts to each package's history stable libraries like lodash or isarray won't be flagged as abandoned just because they're mature and feature-complete. A low-activity library that's genuinely "done" is scored differently than an abandoned project with open CVEs.
Alert Noise
This was our biggest design challenge! Most tools create alert fatigue by treating all vulnerabilities equally. Our approach:
Fully configurable risk model - adjust weights to match your risk tolerance
Customizable thresholds - set your own scoring bands for High/Medium/Low risk
Build-fail policies you control - decide what fails CI/CD vs. what's just tracked
EU CRA Alignment
We built CRA compliance in from day one. ZSBOM meets the mandatory criteria: machine-readable format, vulnerability tagging with traceback connectivity, and comprehensive component mapping including all transitive dependencies. This approach has been validated by university researchers results published on our GitHub (v0.9).
Happy to show you a demo if you want to see the scoring in action on a real codebase! 🚀
Gridapps Testimonials
Congrats on the Launch Ram and Team
Evallo
A much needed tool! Checking it out today!
Trace-AI
@pramodgeorgehq looking forward to your feedback! Thanks for the comment.