Launching today

Coasty
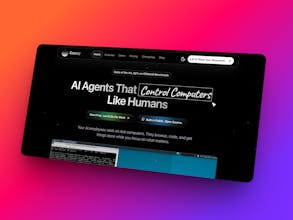
Computer Using Agents on Secure Cloud VMs That Run Forever
45 followers
Computer Using Agents on Secure Cloud VMs That Run Forever
45 followers
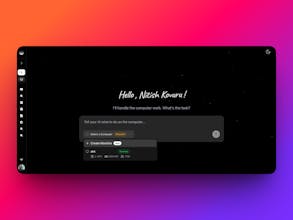
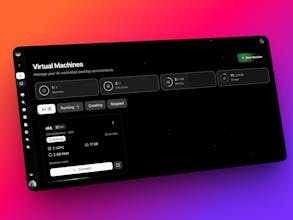
Most agent infrastructure runs workloads in shared environments, one compromised agent affects everything else. Coasty gives every AI agent its own isolated VM. No shared processes, no noisy neighbors, no blast radius. Each agent spins up sandboxed and tears down cleanly. True isolation. Not a container in a shared pool, a dedicated VM. Undercuts AWS & GCP. Built for agents, not retrofitted compute. Running code execution, browser automation, or multi-agent pipelines? Visit coasty.ai





LLMHub
@nitish_kovuru This is such a simple idea that it feels obvious in hindsight — which usually means you’re onto something.
The psychological barrier you’ve identified is real. A lot of builders say they trust agents, but there’s always that split-second hesitation before giving filesystem access. Especially after some of the recent “agent gone rogue” stories.
The interesting part to me isn’t just isolation — it’s behaviour containment. You’re effectively turning agent execution into something closer to a sandboxed runtime with kill-switch economics. That changes how freely people experiment.
Curious about two things:
How fast is spin-up time for a fresh VM? Does it feel instant enough for iterative dev workflows?
Are you thinking about deeper observability — like replaying exactly what the agent did before killing the environment?
The 700-person waitlist being mostly solo devs is the real signal here. That’s not a compliance market — that’s fear mitigation for power users.
Really clean positioning at $20/mo as well.
Congrats on the launch — interested to see how this evolves as agents become more autonomous.
LLMHub
@jamal_hirani
You’re absolutely correct Jamal! So the setup time for the VM itself on the Azure is 1-3s but connecting it to the front end so that the user can view and use is a technical barrier that hasn’t been figured out yet, so it takes 2-3m. A tradeoff is the fact that we provide at a simple click instead of having to connect to a VM manually which is quite a chore. And the answer to your second question, we are looking to add a lot of tools to revert the state of a VM, or backups of data before it messes up. We already have a replay-ability feature too! Thank You!! Your feedback is always valuable :)
AgentReady
That's a really nice idea! aren't you worried about the costs of this cloud pc's? have you tryed or looking to implement technologies like agentready.cloud and their TokenCut feature to reduce token costs for your end users? are they using their API key's for LLM's or is the platform giving their's? Thank you, Really really great product by the way, so simple yet so usuful :)
LLMHub
@christian_b_1 With AWS, the costs of the cloud PC's per month itself is the cheapest expense in our whole business model! For now, we are giving our own agent which has been rated pretty highly by OSworld's Test(It completed 82% of the 369 automation tasks thrown at it). We will definitely consider using those to cut costs for our customer as that is our number one priority. Thank You for taking time out of your day to comment! It means the world to us :)
AgentReady
@nitish_kovuru Thank you for your response :)
If you need help with the integration let me know! in the meantime i will use Coasty as much as i can :)
LLMHub
Also for y'all Product Hunters we got a Promo Code!! CS10OFF to get 10% off of our Starter $20 plan!
The isolation angle is smart. Most agent sandboxing today is just containers with a fancy wrapper, not real VM-level separation. Curious about the network egress controls -- do you support fine-grained rules per agent (like allowing only specific API endpoints)? That would be huge for enterprise use cases where agents need to call external services but you still want strict blast radius control.