
Device Activity Tracker
How (almost) any phone number can be tracked via WhatsApp
1 follower
How (almost) any phone number can be tracked via WhatsApp
1 follower
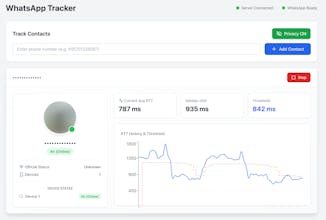
Device Activity Tracker is an open-source proof-of-concept that shows how you can infer a phone’s activity state via WhatsApp & Signal — using only timing information from “ghost” reactions.

Free
Launch Team

Wispr Flow: Dictation That Works Everywhere — Stop typing. Start speaking. 4x faster.
Stop typing. Start speaking. 4x faster.
Promoted
Maker
📌Report
