Launched this week

PatchWatch
Security patch alerts without the noise
3 followers
Security patch alerts without the noise
3 followers
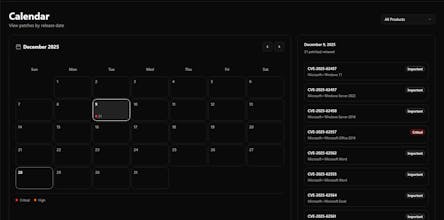
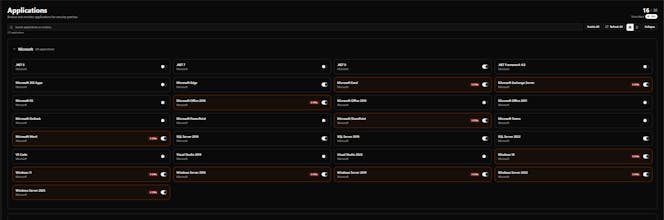
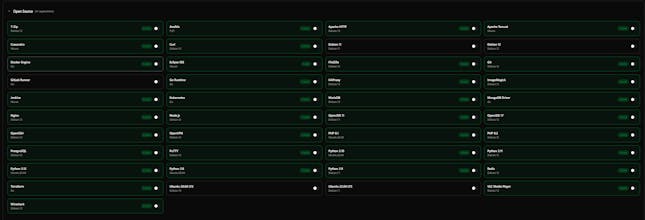
PatchWatch helps security and IT teams stay on top of critical security patches without drowning in alerts. Instead of checking multiple sources manually, PatchWatch aggregates security advisories from Microsoft MSRC, NVD, and OSV into one clean dashboard. Built for patch engineers, security teams, MSPs, and IT admins who want clarity, not noise. PatchWatch is currently in early access & feedback from real practitioners is highly welcome.