
HEX-IAM GitHub v0.1.0 initial release
https://www.hexalgon.site
2 followers
https://www.hexalgon.site
2 followers
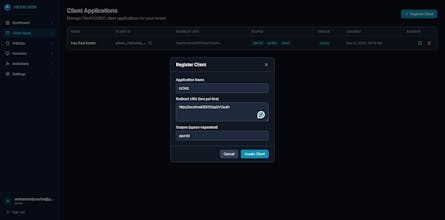
HEX IAM - High-performance IAM with sub-millisecond authorization via policy-embedded JWTs. No database lookups needed. O(1) authorization checks (~1μs) Full OAuth 2.0/OIDC provider Multi-tenant with PostgreSQL RLS Bloom filter token revocation Async audit logging (SOC 2 ready) Built with FastAPI, PostgreSQL, Redis. Docker-ready. Perfect for SaaS platforms, microservices, and teams avoiding vendor lock-in. Apache 2.0 licensed. One-command deployment. Because IAM shouldn't be slow OR expensive.








Hey There!
I built HEX IAM because I got frustrated with the IAM performance vs. cost trade-off.
The core insight: Stop querying databases for every authorization check. Embed policies directly in JWT tokens using bitwise operations.
Result: Authorization in ~1 microsecond instead of 5-50ms. That's 5000x faster.
What's included:
✅ Complete REST API with OpenAPI docs
✅ React admin portal
✅ OAuth 2.0/OIDC provider (use as SSO)
✅ Multi-tenant architecture
✅ Docker deployment (one command)
✅ Full source code + documentation
Tech stack: Python 3.12+ | FastAPI | PostgreSQL | Redis
Perfect for: SaaS platforms, microservices, teams wanting data ownership and avoiding vendor lock-in.
Trade-off to know: Policy changes take effect on token refresh (1-hour TTL). For most apps, this is acceptable for massive performance gains.
License: Apache 2.0 - 100% free forever.
Open to feedback, questions, and contributions. Let me know what you think!