Launching today

Airlock
Monitor, audit, and intercept every agent action.
1 follower
Monitor, audit, and intercept every agent action.
1 follower
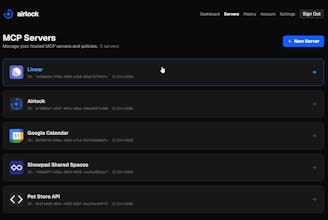
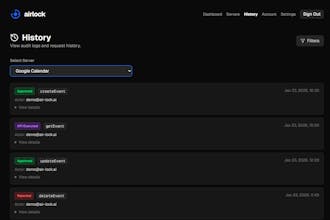
Airlock gives agents secure access to your tools - in minutes, not months. Deploy ready-made MCP servers (Google Calendar, Stripe, etc.) or convert any OpenAPI spec. All your agent governance in one place: approval workflows, PII redaction, credential management, and complete audit trails. Block sensitive actions until humans approve them. Redact PII before it reaches LLM providers. Never expose your real API keys. Zero code changes. Total visibility. Ship autonomous agents with confidence.


Free Options
Launch Team / Built With

AssemblyAI — Build voice AI apps with a single API
Build voice AI apps with a single API
Promoted
Maker
📌Report