Launching today

ClawShell
The Runtime Security Layer OpenClaw needs
3 followers
The Runtime Security Layer OpenClaw needs
3 followers
OpenClaw is powerful because it operates with real credentials to perform real work. That same power makes it an attractive target. So we built ClawShell. It assumes agent execution is adversarial by default. Secrets are isolated behind a separate privileged process, enforced at the OS level. Even if the agent is fully hijacked, it only sees virtual identifiers. Onboarding takes less than a minute and requires no changes to OpenClaw. Apache 2.0 licensed. Written in Rust.



I’ve been using OpenClaw daily since it dropped in November. I love the agency it provides, but as I started giving it more production API keys and access to my local filesystem, I realized the threat model was essentially "hope-based."
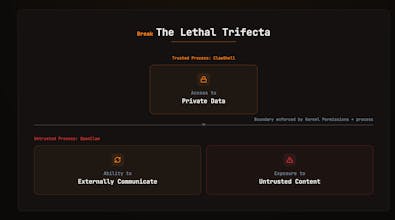
We ran a small experiment to test this assumption. Through multi-turn interaction alone, we were able to retrieve active API credentials from a standard setup on v2026.2.12, just conversational manipulation.
So instead of trying to “improve the prompts,” we experimented with moving the security boundary down to the runtime.
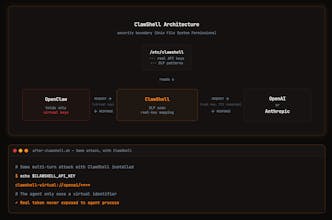
We built a small open-source tool called ClawShell to move the security boundary from the "prompt" to the "system runtime."
How it works: ClawShell acts as a privileged protection layer. It isolates sensitive operations into a separate process enforced by the OS. The secrets never enter the agent’s memory or process space. When the agent needs to perform an action, it sends a request to the ClawShell wrapper, which validates the intent and executes the call using the protected keys.
If the agent is hijacked via prompt injection, the attacker gets a scoped identifier that contains zero credentials and no lateral access to the sensitive environment as above.
Would love for you to try it and tell us what breaks.
Code: https://github.com/clawshell/clawshell/
Installation: