Launched this week

Kleidia
Manage YubiKeys at scale, in your own infrastructure
3 followers
Manage YubiKeys at scale, in your own infrastructure
3 followers
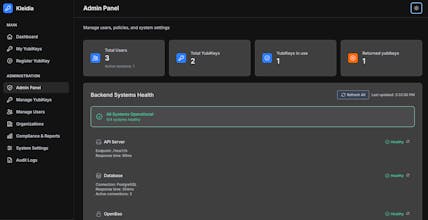
Kleidia is a self-hosted control plane for managing YubiKeys at scale. It runs in your own Kubernetes cluster, plugs into your existing PKI, AD/EntraID and replaces scripts and spreadsheets with standard, auditable workflows.


I’m a seasoned infra & platform architect, not a full-time developer. I went looking for a way to manage YubiKeys and FIDO2 at scale in a NIS2-style environment… and kept running into the same friction: solutions are often priced per user/credential (so cost scales directly with rollout size).
I also evaluated the established players (Versasec, Intercede, 0pass, Pointsharp). They can cover a lot of ground (credential lifecycle, self-service, integrations).
So I built Kleidia: a self-hosted control plane for YubiKeys — focused on making hardware MFA operational and auditable in regulated environments, without turning rollout into a licensing cliff or a bespoke scripting project.
What Kleidia helps teams solve
– Replace fragile scripts & manual handling with a real lifecycle workflow (issue/assign/rotate/revoke)
– Make YubiKeys practical for everyone, not just a small admin group (while keeping policy control)
– Reduce helpdesk load via safe end-user self-service (within admin-defined guardrails)
– Make audits less painful with an explicit, queryable trail of key + certificate operations
How Kleidia is intentionally different
– Kubernetes-native: deployed into your cluster via Helm (on-prem, cloud, air-gap)
– Flat annual license: 19,000 €/year, unlimited users & keys (predictable rollout economics)
– Works with your existing CA: OpenBao/Vault acts as an intermediate PKI engine under your current hierarchy
– Workstation-local key ops: lightweight agent talks to the YubiKey locally (Windows & macOS)
– Enterprise identity fit: integrates with AD / Entra ID via OIDC providers (Keycloak etc.)
What Kleidia does
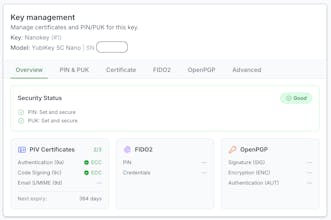
– Manages the lifecycle of YubiKeys (enrolment, assignment, PIV certs, FIDO2)
– Gives admins visibility into registered certificates + revocation flows
– Provides policy-scoped end-user self-service journeys
– Produces a full audit trail of key and management operations
How it runs
– Kubernetes + Helm
– PostgreSQL for metadata, OpenBao/Vault for secrets + CA keys
– Optional “managed appliance” for orgs that want a dedicated cluster operated in their environment
How it was built
I lean heavily on LLM tools for wiring and boilerplate, but the architecture, security model, and tests are deliberate. I treat agents as fast assistants — not a substitute for system design.
Kleidia is already in PoC with government agencies, where the recurring themes are: replacing manual processes, staying within sovereignty rules, and making hardware MFA auditable.
I’d love feedback from security / IAM / PKI folks, anyone who has rolled out YubiKeys or FIDO2 at scale, and people dealing with NIS2-like regulations. Even if you never use Kleidia, I’m happy to share what I’ve learned about making hardware keys practical in regulated environments.