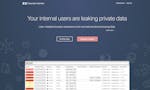
Do you use Extension Monitor?
What is Extension Monitor?
Browser extensions are leaking private data about your organization. Many request an excessive amount of data from users and resell it. Extension Monitor helps IT and Security teams track browser extension installations and threats in real-time.
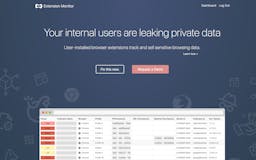
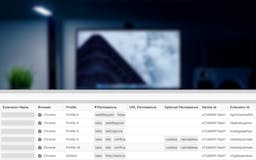
Recent launches
Extension Insights Newsletter
Extension Monitor offers a monthly newsletter of insights into the Chrome Web Store. Stay up to date on the newest, most popular, and fastest growing extensions.
Pro packages include raw CSV data to incorporate into your own workflow.
Extension Monitor
Browser extensions are leaking private data about your organization. Many request an excessive amount of data from users and resell it. Extension Monitor helps IT and Security teams track browser extension installations and threats in real-time.